Onboarding Prerequisites
Contact Information
In order to submit the requests for the ‘Customer Key’ (encryption) portion of your configuration to Microsoft, we need two contacts from your company. We need name, email and phone – and they should match the criteria specified by Microsoft below:
Two (2) contacts who will be the individuals contacted by us/Microsoft who are your Company Principals aka C-Level Executives and who are not admins on the Key vaults in case either of your subscriptions have any issues. For the email address, it is recommended to provide an email address that is not going to be Customer Key Encrypted, this could be a secondary internal mailbox that will only be used for this purpose and will not have a Data Encryption Policy assigned to it.
User Role Assignments
Provide all users that should be assigned the following roles:
| Role | Description |
|---|---|
| Global Administrator | Full access to all aspects of tenant |
| Authentication Administrator, User Administrator | User administrators are responsible for managing all aspects of users in Azure Active Directory, including onboarding, offboarding, password resets & suspend users. |
| Intune Administrator, Office Apps Administrator, Cloud Device Administrator, Teams Devices Administrator | Users that will have the ability to manage enrolled devices. This includes changing users, modifying software, managing updates and defender, among any other endpoint / device items. |
| Exchange Administrator | Responsible for e-mail configurations. They would have the ability to track down lost or false/positive spam emails, add domains to safe or blocked senders list, configure forwarding, etc. |
| License Administrator, Billing Administrator | Users are able to manage and transfer licenses from one user to the other, as well as order additional licenses when necessary. |
| Privileged Role Administrator | Responsible for approving or denying privileged access escalations and software installations. |
Group Assignments
Provide all users that should be assigned the following group:
| Group | Type | Description |
|---|---|---|
| Compliance Managers | Role-based Security | Users in this group will have the Compliance & Compliance Data Administrator roles assigned. Users in this group will be assigned to role access reviews as well as guest access reviews. They will also have access to Microsoft Sentinel logs and reports. |
| Compliance Alerts | Distribution | All members of this distribution group will receive alerts when there are any notices or issues related to compliance. This includes but is not limited to devices falling out of compliance, user risk detections, role elevations, etc. |
| Authorized Managers | Security | Users in this group are authorized to make requests on behalf of the organization. These requests include user onboardings, offboardings, configuration changes & role elevation requests. |
| Local Device Administrators | Security | Users in this group can be made local device administrators on an as-needed basis using Privileged Identity Management requests. |
Pre-approved applications
The security baseline for endpoints leverages AppLocker for application control. The default AppLocker policies are designed to block all applications for non-admin users and includes a handful of whitelisted applications out of the box. Those whitelisted applications are:
- All files located in the Program Files folder
- All files located in the Windows folder, with exception of applications requiring elevated privileges
- Windows Defender Executables
- Microsoft OneDrive
Required information for application whitelisting
To whitelist other applications, we’ll need some basic information about the executables.
- Run powershell with administrative privileges
-
Run the following command on each EXE / DLL / file that needs to be added to the AppLocker whitelist:
Get-AppLockerFileInformation -Path "C:\path\to\file\file.exe" | export-csv "C:\whitelist_info.csv" -Append -NoTypeInformationAlternatively, this command can be run on all files in a directory by using:
Get-AppLockerFileInformation -Directory C:\Windows\system32\ -Recurse -FileType exe, script, dll | export-csv "c:\whitelist_info.csv" -Append -NoTypeInformation - Every file/folder that this command is run on will be appended to
c:\whitelist_info.csv. Once the Get-AppLockerFileInformation command has been run on all files, please send an email with the CSV file attached to it to: support@nimbus-logic.us with the subject “AppLocker info for yourdomain.com.”
Required information for USB whitelisting
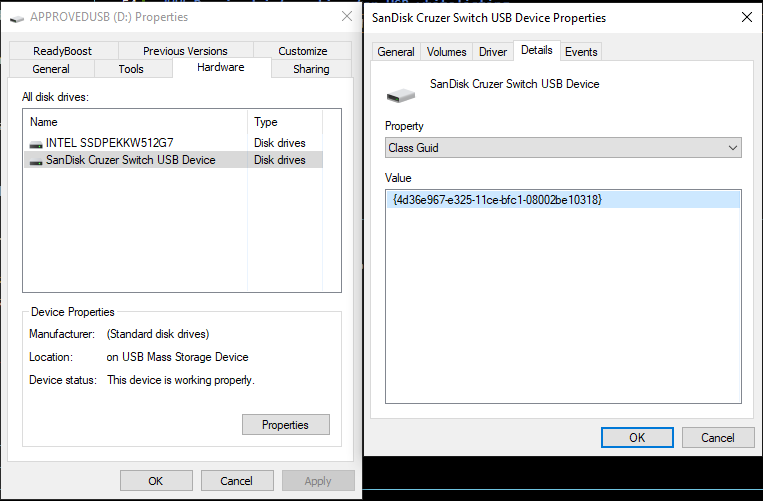
To whitelist USB Disk or Windows Portable Devices, we require both the Device Instance Path and Class GUID for the device. To get this information, on a non-onboarded / locked down PC, please perform the following steps:
- Plug the USB device in & browse to it in your file explorer.
- Right click on the the device and go to “Properties”
- Navigate to the Hardware tab, and select the drive under “All disk drives.” These steps may vary slightly at this point depending on the device type.
- Click on “Properties” at the bottom of the window, and then open the “Details” tab on the subsequent window.
- For property, select “Device Instance Path”, and copy/paste the value somewhere for later use. Do the same for “Class GUID”. If there are multiple devices listed in this window like in the screenshot below, please provide these values for both.
- Provide this data do your device / compliance administrator, and have them open a ticket by emailing support@nimbus-logic.us and provide the data gathered above.
- If you require further assistance or your device does not display as described above, please open a ticket by emailing support@nimbus-logic.us, and we’ll be happy to work with you to acquire the necessary information.
Device Prerequisites
Required prerequisites to attain device compliance:
- TPM 2.0+
- Secure Boot enabled
If a device does meet the required specifications, then it cannot be within the scope of compliance.
