Audit & Accountability
Overview
Azure has several offerings that have been implemented to facilitate audit & accountability management including Azure Active Directory, Azure Monitor, Azure Sentinel and Log Analytics Workspace.
-
Azure Active Directory is an identity and access management-as-a-service (IDaaS) solution that combines single-on capabilities to any cloud and on-premises application with advanced protection.
-
Azure Monitor helps collect, analyze, and act on telemetry data from your Azure and on-premises environments. Azure Monitor helps you maximize performance and availability of your applications and proactively identify problems in seconds.
-
Azure Sentinel is a scalable, cloud-native, security information event management (SIEM) and security orchestration automated response (SOAR) solution.
-
Log Analytics Workspace is a unique environment for Azure Monitor log data. Each workspace has its own data repository and configuration. Data sources and solutions are configured to store their data in a workspace.
Log User Actions
Azure Active Directory (Azure AD) records all user activity in the Azure portal. The audit logs report consolidates the following reports:
- Audit report
- Password reset activity
- Password reset registration activity
- Self-service groups activity
- Office365 Group Name Changes
- Account provisioning activity
- Password rollover status
- Account provisioning errors
Review user activity in Azure AD via the steps below: For more information, see Find activity reports in the Azure portal.
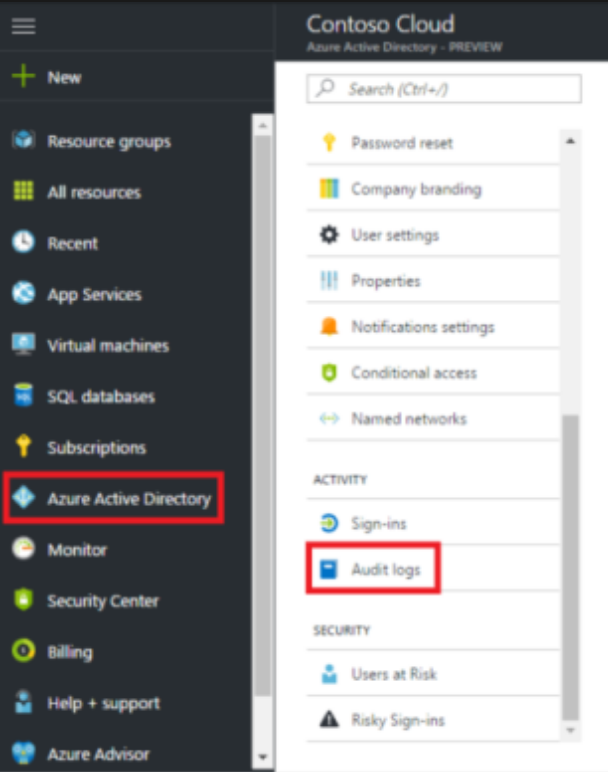
Navigate to the Azure portal.
Select your directory from the top-right corner, then select the Azure Active Directory blade from the left navigation pane.
Select Audit logs from the Activity section of the Azure Active Directory blade.
Enable Resource Logging
All cloud services & enrolled endpoints are configured to have full logging implemented and streamed to Microsoft Sentinel. Microsoft Sentinel is implemented to serve as the Security Information and Event Management (SIEM) platform.
Access to Microsoft Sentinel is restricted and available only to users in the Global Administrator & Compliance Managers groups.
Security Baseline: Microsoft Sentinel has been configured with the following data connectors included by default as part of the security baseline configuration
- Azure Active Directory
- Azure Active Directory Identity Protection
- Microsoft 365 Defender
- Microsoft 365 Insider Risk Management
- Microsoft Defender for Cloud Apps
- Microsoft Defender for Endpoint
- Microsoft Defender for Identity
- Microsoft Defender for Office 365
- Office 365
- Security Events via Legacy Agent
Synchronize Time Stamps
Time sync is important for security and event correlation. Time accuracy between multiple computer systems is achieved through synchronization. Synchronization can be affected by multiple things, including reboots and network traffic between the time source and the computer fetching the time.
Security Baseline: Your security baseline includes a device configuration profile that sets the time provider of the windows device to
time.windows.com
Centralize Logging
Microsoft Sentinel has been deployed and configured to serve as the SIEM platform. Data sources from all Microsoft cloud services as well as all managed endpoints are configured to stream log data into Sentinel.
You can view the logs in the built-in dashboards and start building queries in Log Analytics to investigate the data. For more information, see Quickstart: On-board Microsoft Sentinel.
Stream Logging Events
Microsoft Sentinel creates the connection to services and apps by connecting to the service and forwarding the events and logs to Microsoft Sentinel.
The following data sources are connected to Microsoft Sentinel as part of the security baseline.
- Azure Active Directory
- Azure Active Directory Identity Protection
- Microsoft 365 Defender
- Microsoft 365 Insider Risk Management
- Microsoft Defender for Cloud Apps
- Microsoft Defender for Endpoint
- Microsoft Defender for Identity
- Microsoft Defender for Office 365
- Office 365
- Security Events from Endpoints
Alert on Logging Failures
Azure health alerts have been configured for Log Analytics services to send an alert for any of the following events.
- Service Issue
- Planned maintenance
- Health advisories
- Security advisory
In the event a health event has been triggered, an email will be sent to members in the ComplianceAlerts distribution group.
Set Logging Admin Controls
Only authorized personnel can access administrative logs stored in Microsoft Sentinel. Authorized personnel are defined as any of the following
- Global Administrator role
- Compliance Managers group members
- Compliance Administrator role
- Compliance Data Administrator role
Protect Audit Logging
Audit logging is protected by managing access to log data, encrypting logs with customer-based encryption keys and setting retention policies.
Review Logs
Using Microsoft Sentinel, you can visualize and monitor log data using a variety of methods.
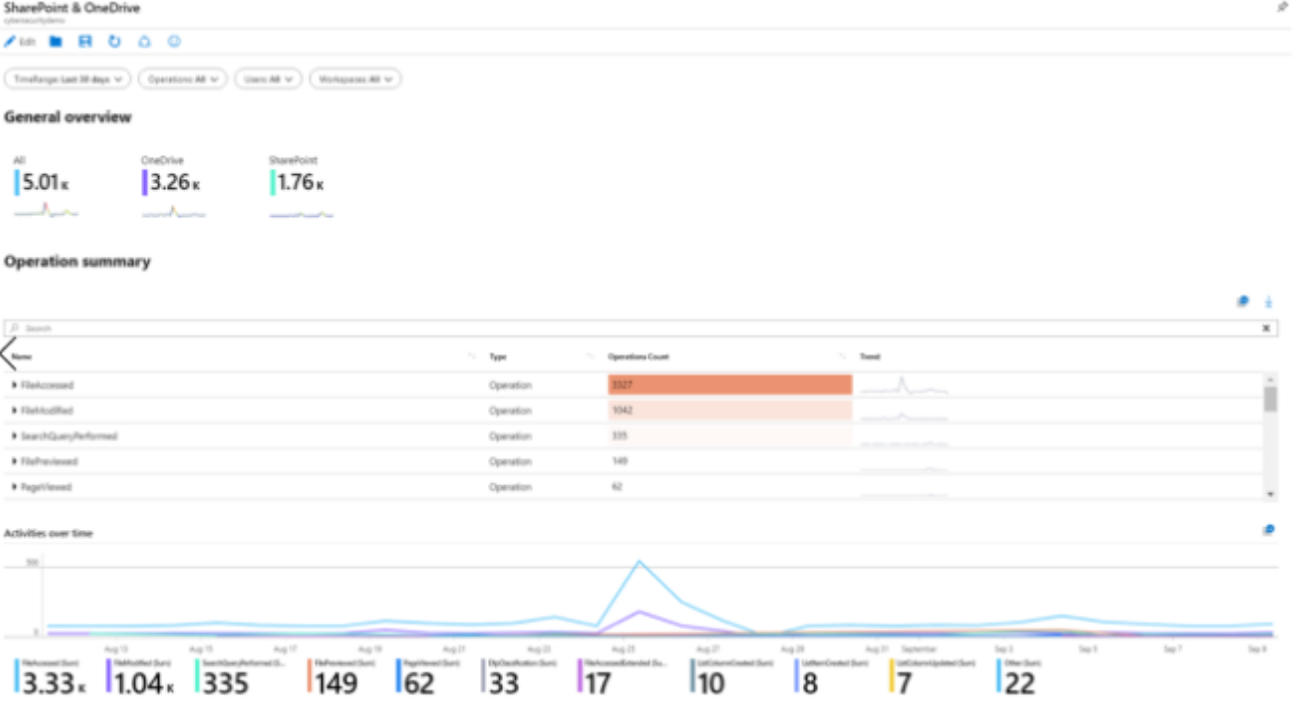
Log Editor
You can query and view raw log data by simply navigating to the Logs link in the Microsoft Sentinel dashboard. Kusto Query Language (KQL) is the language you will use to work with and manipulate data in Microsoft Sentinel. For information, best practices, and a cheat sheet, see Kusto Query Language in Microsoft Sentinel
Workbooks
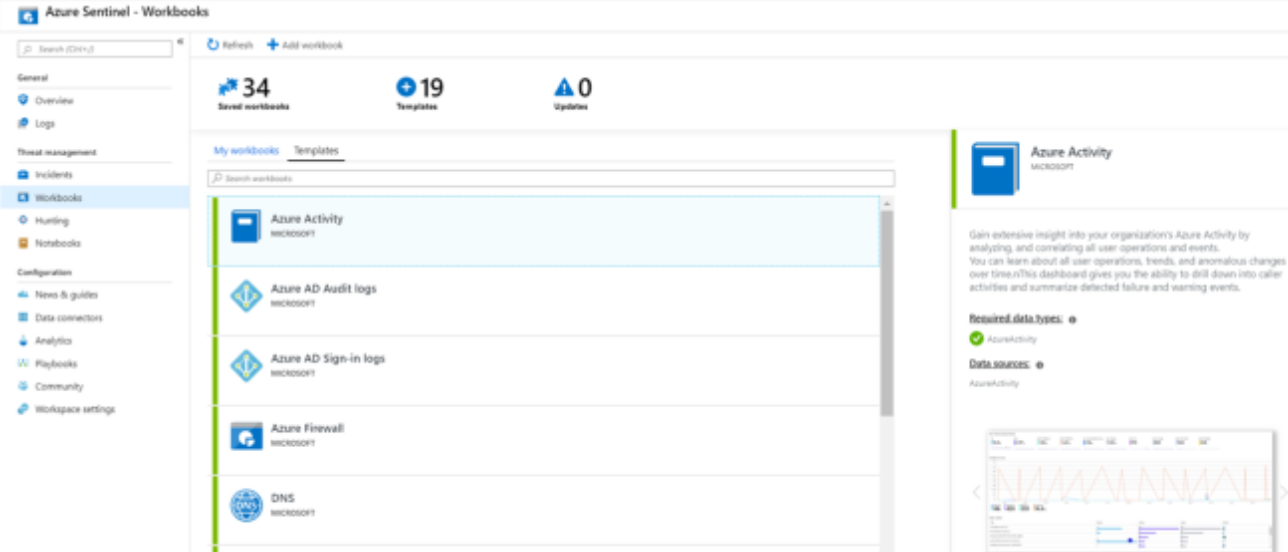
Microsoft Sentinel allows you to create custom workbooks across your data, and also comes with built-in workbook templates to allow you to quickly gain insights across your data as soon as you connect a data source. You can create custom workbooks or follow the steps below to start with a built-in workbook. For more information, see Tutorial: Visualize and monitor your data.
- Sign into the GCC Azure Portal or GCC-High Azure Portal
- Search for and select Microsoft Sentinel.
- Go to Workbooks and then select Templates to see the full list of Microsoft Sentinel built-in workbooks. To see which are relevant to the data types you have connected, the Required data types field in each workbook will list the data type next to a green check mark if you already stream relevant data to Microsoft Sentinel.
- Click View workbook to see the template populated with your data.
- To edit the workbook, select Save, and then select the location where you want to save the json file for the template.
- Select View workbook. Then, click the Edit button at the top. You can now edit the workbook and customize it according to your needs.
- After you make your changes, you can save the workbook.
- You can also clone the workbook: Select Edit and then Save as, making sure to save it with another name, under the same subscription and resource group. These workbooks are displayed under the My workbooks tab.
Investigate Abnormal Activity
Microsoft Sentinel provides for out-of-the-box built-in templates to analyze log data any notify compliance managers when something suspicious happens. These templates were designed by Microsoft’s team of security experts and analysts based on known threats, common attack vectors, and suspicious activity escalation chains.
The following templates are enabled as part of your security baseline.
- Authentication Methods Changed for Privileged Account
- Create incidents based on Azure Active Directory Identity…
- User agent search for log4j exploitation attempt
- Suspicious application consent similar to O365 Attack Toolkit
- Create incidents based on Microsoft Defender for Endpoint alerts
- Azure AD Role Management Permission Grant
- Create incidents based on Microsoft Defender for Identity
- Privileged Accounts - Sign in Failure Spikes
- Account Created and Deleted in Short Timeframe
- Brute force attack against Azure Portal
- MFA disabled for a user
- Malware in the recycle bin
- Mail.Read Permissions Granted to Application
The enabling of these templates will automatically search for any activity that looks suspicious across your environment. The alerts generated by these templates will create incidents that will create a support ticket with Nimbus Logic automatically.
For more information, see Tutorial: Detect threats out-of-the-box.
Optimize & Report
As part of your security baseline, automated compliance reports are aggregated on a weekly basis and emailed to all necessary stakeholders. The automated compliance report includes:
- Statistics for active, admin & stale users.
- Device listing for devices not identified as being compliant
- User listing identifying users with sign-in activity over 30 days ago
- Endpoint malware report
- Defender agent status
