Identity and Access Management (IAM)
Overview
Azure has several offerings to facilitate asset & configuration management including Azure Security Center, Azure Active Directory, Azure AD Privileged Identity Management, Azure Policy and Azure Information Protection
-
Azure Active Directory is an identity and access management-as-a-service (IDaaS) solution that combines single-on capabilities to any cloud and on-premises application with advanced protection.
-
Windows Hello for Business replaces passwords with strong two-factor authentication on devices. This authentication consists of a new type of user credential that is tied to a device and uses a biometric or PIN.
-
Azure AD Privileged Identity Management is a service that enables you to manage, control, and monitor access to important resources in your organization. These resources include resources in Azure AD, Azure, and other Microsoft Online Services like Office 365 or Microsoft Intune.
-
Azure Information Protection helps secure email, documents, and sensitive data that you share outside your company.
Secure Authentication (MFA)
Azure AD MFA for Microsoft Apps & Services
Azure Active Directory provides the capabilities to set granular authentication controls for users, applications and services. Multi-factor authentication is enforced for all users, administrators and non-administrators, and requires users to register multiple authentication methods. Those authentication methods are:
- Password
- Microsoft Authenticator App
- SMS text message
- Voice Call
Security Baseline: MFA is enforced for all tenant users and Azure AD cloud applications and services using the conditional access policy,
NIST - GRANT - MFA For All Users
It’s important to note that Azure AD MFA does not apply to your device login, ie. Windows desktop. For device level multi-factor authentication, Windows Hello for Business is configured and enforced.
Windows Hello for Business (WHFB)
Windows Hello for Business replaces passwords with strong two-factor authentication on PCs and mobile devices. This authentication consists of a new type of user credential that is tied to a device and uses a biometric or PIN. Windows Hello for Business combined with Azure Active Directory joined devices makes it easy for users to securely access cloud-based resources using a strong, two-factor credential.
Security Baseline: Windows devices must setup Windows Hello for Business to be marked as compliant. For instructions on setting up WHFB, see the Enrolling Endpoints section within the Onboarding Guide
Role Based Access Control (RBAC)
Access management for cloud resources is a critical function for any organization that is using the cloud. Role-based access control (RBAC) helps you manage who has access to what functions and allows segregation of duties within your team.
Security Baseline: The following groups and roles have been configured for your tenant.
| Group | Role | Description |
|---|---|---|
| Compliance Managers | Compliance Administrator, Compliance Data Administrator | Users are responsible for checking audit logs, monitoring reporting tools, and guiding users through remediation processes when compliance is not met. |
| Billing and License Administrators | License Administrator, Billing Administrator | Users are able to manage and transfer licenses from one user to the other, as well as order additional licenses when necessary. |
| User Administrators | Authentication Administrator, User Administrator | User administrators are responsible for managing all aspects of users in Azure Active Directory, including onboarding, offboarding, password resets & suspend users. |
| Endpoint Administrators | Intune Administrator, Office Apps Administrator, Cloud Device Administrator, Teams Devices Administrator | Users that will have the ability to manage enrolled devices. This includes changing users, modifying software, managing updates and defender, among any other endpoint / device items. |
| Exchange Administrators | Exchange Administrator | Responsible for e-mail configurations. They would have the ability to track down lost or false/positive spam emails, add domains to safe or blocked senders list, configure forwarding, etc. |
| Approvers | Privileged Role Administrator | Responsible for approving or denying privileged access escalations and software installations. |
| Compliance Alerts | None, Mail-enabled security group | All members of this group will receive alerts when there are any issues related to compliance. This includes but is not limited to devices falling out of compliance, user risk detections, etc. |
| All Employees | None | All organizational users (Dynamic) |
| Company Guests | None | Company guests |
Least Privilege
Role Based Access Control is implemented in your organization. The roles help to manage who has access to Azure resources, and what areas they have access to. These roles, groups and responsibilities were all defined by your onboarding team at the time of enrollment into Compliance as a Service. The Azure portal allows the appropriate users to review who has access to Azure resources and their permissions. This configuration assigns an Azure policy definition that helps to monitor your overall environment.
Security Baseline: Compliance Managers can review Active and Eligible role assignments anytime by navigating to Azure AD Portal > Search for Privileged Identity Management > Azure AD roles > Assignments
Secure Administrative Rights
Administrative rights are secured with Azure Active Directory Privileged Identity Management (PIM). This feature provides tight control over administrative rights including conditional access, eligibility windows, global admin approvals, admin time windows and logging.
Organization Administrators
Organization administrators are initially identified as a part of onboarding onto the compliance as a service program. Administrative roles are assigned an Eligible role, and require activation.
Security Baseline: Privileged Identity Management (PIM) has been configured and is enforced for all administrator roles. Authorized users will have these administrator roles available within their Eligible Assignments. Activation of these eligible assignments requires the following:
- Re-authentication with MFA
- Specifying duration of activation
- Brief justification of elevation
Nimbus Logic (CSP) Administrators
Nimbus Logic, serving as the Cloud Service Provider (CSP), will require Global Administrator role for some support requests. Upon initial setup, Nimbus Logic will create a unique administrator account for each support technician and will follow the same PIM procedures to elevate roles only when necessary.
Security Baseline: Nimbus Logic administrators will have the following role assignments permanently assigned:
Active Roles
- Security Reader
- Report Reader
Eligible Roles (Elevated when is necessary for support)
- Global Administrator
- Exchange Administrator
- Endpoint Administrator
The process to request elevated access can be found below.
Requesting Elevated Access
Role eligibility is initially determined by your organization as part of onboarding. Eligible roles can be made active at any time with the following steps.
-
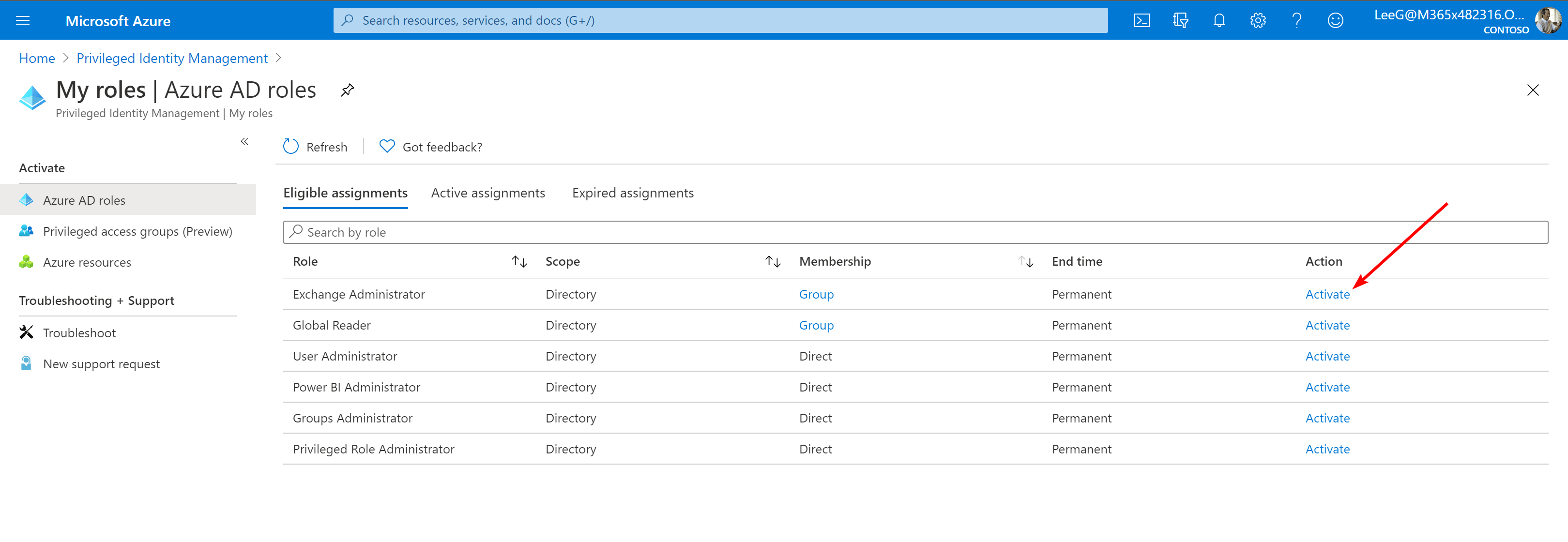
Login to Azure AD Privileged Identity Management (GCC) or Azure AD Privileged Identity Management (GCC High).

- Locate the desired role to active and click the Activate link
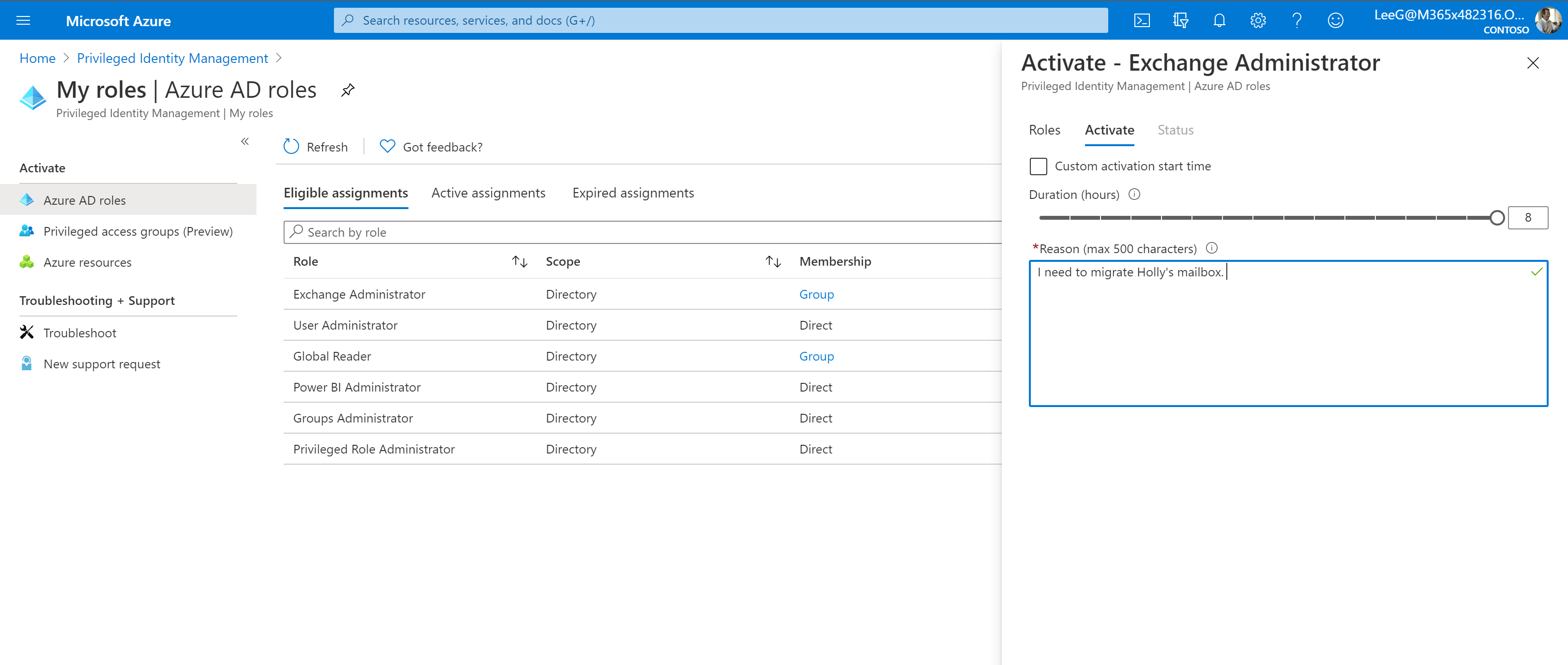
- Choose your desired duration for role assignment and a brief justification
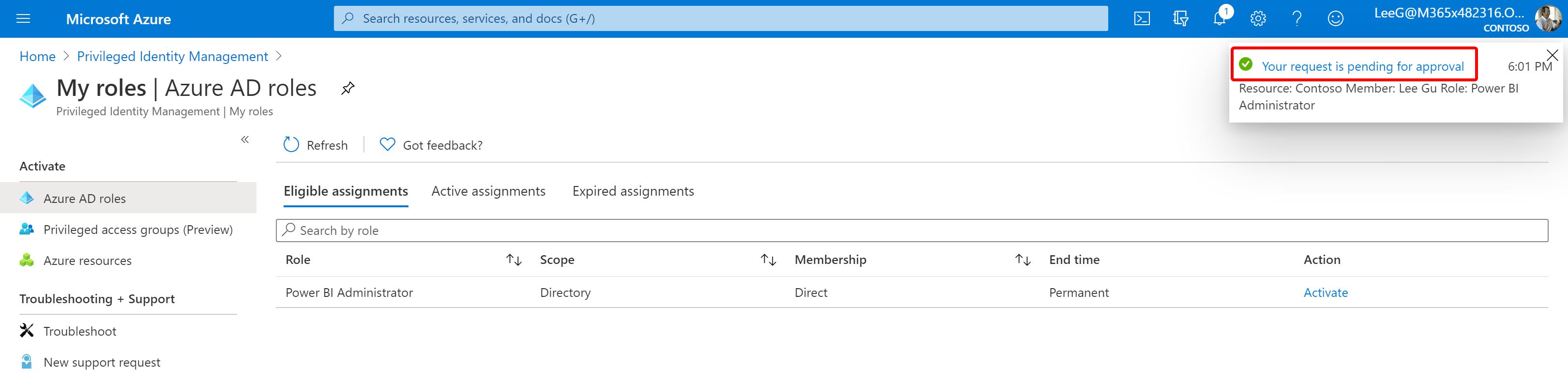
- If applicable to the requested role, a notice will be sent to authorized approvers within your organization. Upon their approval you will receive notification by email and your role will automatically be activated. If approval is not required for the desired role, your activation will automatically be granted immediately.
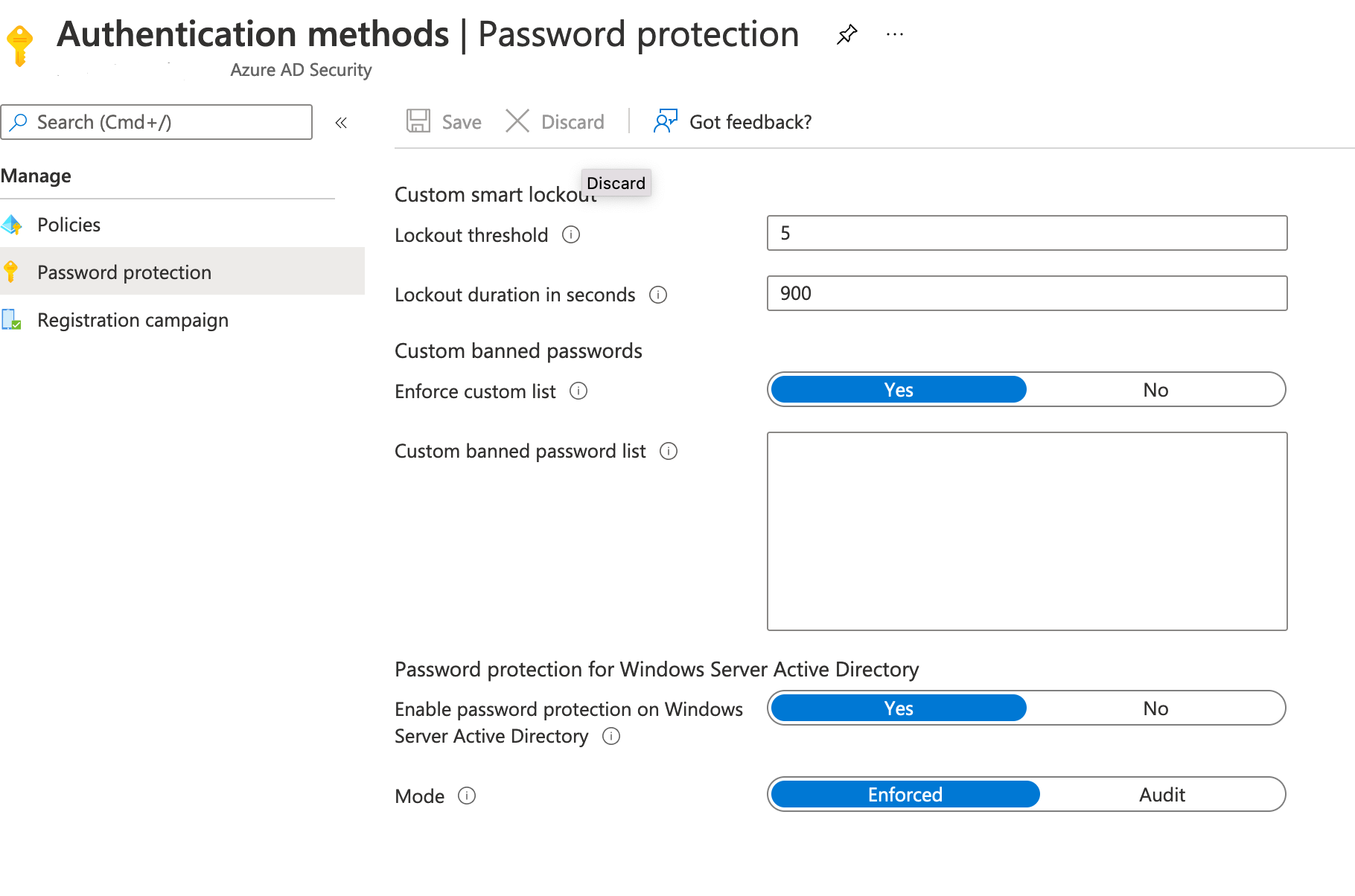
Lockout Threshold
Lockout threshold mitigates brute force attacks against passwords. This limits how many incorrect guesses someone can make before the account locks out.
Security Baseline: The following settings have been configured for your Azure AD Tenant
- Lockout threshold:
5- Lockout duration in seconds:
900
Inactivity Logoff
-
Organization Users
Sign-in frequency defines the time-period before a user is asked to sign in again when attempting to access a resource. The Azure Active Directory (Azure AD) default configuration for user sign in frequency is a rolling window of 90 days. -
Organization Guests
A conditional access policy has been configured that requires all Guests of an organization to be required to re-login every day.Security Baseline: Guest timeout is defined in the conditional access policy
NIST - SESSION - Guest Timeout
Adaptive Access Control
Microsoft Azure leverages adaptive access control through Azure Active Directory (AAD) conditional access. Conditional Access is the tool used by Azure Active Directory to bring signals together, to make decisions, and enforce organizational policies. Conditional Access is at the heart of the new identity driven control plane.
The following conditional access policies have been configured with your security baseline
-
NIST - BLOCK - Legacy AuthenticationThis policy blocks legacy authentication for all users; legacy authentication is defined as any device using Exchange Active Sync or other
-
NIST - GRANT - MFA For All UsersThis policy requires Multi-factor authentication for All users
-
NIST - GRANT - Guest Web-Only AccessRequires guests to access Office365 using web browser unless they are accessing from a enrolled compliant device
-
NIST - SESSION - Guest Timeout -
NIST - GRANT - Require compliant device for Windows or Mac accessThis policy enforces device compliance (or Hybrid Azure AD join) for these platforms: Windows, macOS
NOTES:
- Azure AD joined or Hybrid Joined devices will be auto-enrolled if configured properly
- Users with personal devices should use the Company Portal app to enroll
- This policy blocks unmanaged device access from desktop client apps (e.g. Outlook, OneDrive, etc.)
-
NIST - BLOCK - High Risk Sign-InsBlocks sign in to ALL cloud applications if the user is designated as a risky sign-in.
HIGH impact when an account has been flagged.
Remote Access
Partner remote access to a network can introduce vulnerabilities if not properly implemented, secured and controlled. Remote access to enrolled endpoints is disabled per Windows default implementation.
Connection Management
Windows Defender Firewall with Advanced Security is an important part of a layered security model. By providing host-based, two-way network traffic filtering for a device, Windows Defender Firewall blocks unauthorized network traffic flowing into or out of the local device.
Security Baseline: Microsoft Defender Firewall is enabled on each endpoint for private and public networks as defined in Endpoint security policy
NIST - Windows 10 Defender Firewall
Data Usage Controls
The security baseline leverages the use of Sensitivity Labels as defined in the following section.
Confidential Data Security
You can secure controlled unclassified information (CUI) and control information flows with Azure Information Protection (AIP). Azure Information Protection is a cloud-based solution that helps your organization organization to classify and optionally, protect its documents and emails by applying labels.
Security Baseline: There are 2 sensitivity labels created as part of your security baseline.
**CUI Encrypt Only**- Encrypts e-mails and files internal to the company’s domain. The scope included in this policy contains files and emails, and will encrypt, as well as mark the contents of the files. Users are able to assign permissions at the time of label application. In MS Outlook, e-mails are encrypted and forwarding disabled only. By default, a water mark (specified at the time of onboarding) will be applied.
**CUI Do Not Forward**- Encrypts and prohibits forwarding of e-mails with this label attached when sending to anywhere external to the company’s domain. In MS Outlook, e-mails are encrypted and forwarding disabled only. By default, a water mark (specified at the time of onboarding) will be applied.
