Solution overview
This overview covers the purpose of Compliance as a Service, its components, and design considerations and decisions.
Purpose of Compliance as a Service (CAAS)
The security baselines established by Compliance as a Service empowers organizations to provide their workforce with secure, flexible, and mobile solutions. It uses native Microsoft technologies that are integrated and provide a quality end-user experience.
About Nimbus Logic
Nimbus Logic is a Registed Provider Organization (RPO) and Microsoft Government Partner that has engineered a secure cloud-based service, based on the Microsoft stack of technologies, to satisfy all of the controls required by CMMC to fast-track your compliance requirements.
Compliance as a Service Components
Compliance as a Service, provided by Nimbus Logic, provides 3 core services to assist organizations with their CMMC compliance journey.
- Microsoft 365 Configuration & Endpoint Onboarding - Much of this compliance guide covers how your Microsoft 365 services and onboarded endpoints are configured to achieve complete NIST 800-171 / CMMC 2.0 L2 compliance. Nimbus Logic has established a security baseline based on the Microsoft NIST 800-171 R2 assessments. Windows 10/11 workstations & compatible mobile devices (iOS/Android) are onboarded and managed with Microsoft Intune for secure Endpoint Management.
- Gap Analysis, Compliance Assessment & Pre-built Policies - The compliance assessment portal will allow you to efficiently perform your Gap Analysis and will automate SPRS score generation, POAM & SSP. Nimbus Logic will assist you in completing your Gap Analysis, providing all the relevant documentation for all in-scope, Microsoft cloud services and managed endpoints.
- Ongoing Real-Time Security Monitoring, Reports & Compliance Support - All endpoints and cloud services will have ongoing real-time security monitoring for compliance, threat & vulnerabilities. Reports will be also delivered on a regular schedule to keep you informed.
Where to start
This overview is suitable for all users as a starting point.
The compliance guide is broken down by the following topics
- Identity & Access Management
- Audit & Accountability
- Asset & Endpoint Management
- Identification & Authentication
- Maintenance & Media Protection
- Recovery & Risk Management
- Security Awareness
- Systems & Communications Protection
- System & Information Integrity
- Reporting & Alerts
- Requirements
For each topic in this guide, the following will be considered:
- A brief overview of the topic and what technologies are implemented
- List of actions taken to satisfy compliance requirements
- How each action is configured
- Any associated training articles and resources
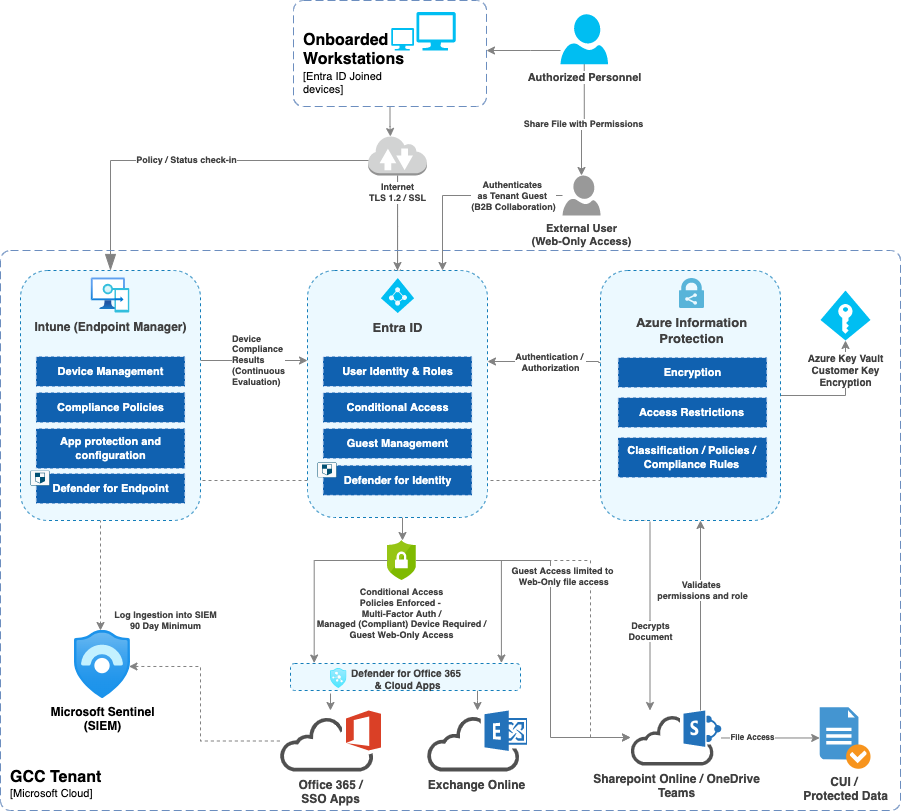
Microsoft 365 compliance components
The compliance guide provides information, rationale and configuration settings for the following components:
- Cloud identity – Azure Active Directory configuration, including Multi-Factor Authentication (MFA) and conditional access, allows log in from anywhere and appropriate security policies to be applied
- Microsoft 365 – Configuration of Exchange Online, SharePoint Online, Microsoft Teams, Whiteboard, Forms and OneDrive for Business allowing cloud-based file storage
- Device management – Management of security and configuration profiles for enrolled devices (includes testing against security baselines and confirmation of security compliance)
- Applications – Delivery and configuration of applications appropriate to the user
- Security stack – Security configuration of Office 365 and endpoint devices to achieve CMMC compliance
- Autopilot deployment – Configuration of Autopilot allows for automated deployment (and redeployment when required) of devices with no user interaction (GCC Community only, not available in GCC High)
- Support – A flexible support model with system administration and role-based access control, whether the support is carried out by in-house staff, third party contractors or a managed service provider.
Microsoft 365 component overview
Information management
The CAAS security model implements all of the following information management tools:
- OneDrive is for data relevant to the individual user, automatically synchronised to the cloud so it is available anywhere and backed up. This data can be personal data that is not relevant or required to be shared with other team members.
- Microsoft Teams is for data to be shared in a read-write format with work colleagues and/or external guests. Every team member has read-write access. People who are not members of the team do not need access. Besides document collaboration team members can chat, use voice and video call, share screens, and attend online meetings.
- SharePoint Online is for data that needs to be published internally. Users may need to access the data in a read-only manner. At this point the data should be moved to SharePoint. SharePoint by default allows for document owners (full control), contributors (read-write) and visitors (read-only). Internal staff and external guests may be added to any of these groups according to the permission they need.
Information protection
Information protection covers the application of labels to documents and emails according to the classification of the content.
The CAAS security model implements Microsoft Information protection for the labeling of documents and emails.
Sensitivity labels create a protective marking within the message header. When combined with Exchange mail flow rules, the subject can be modified to prepend text in the subject according to the sensitivity.
The compliance guide provides guidance about applying Microsoft sensitivity labels. The unified labelling client that underpins Microsoft sensitivity labels is built into Office 365. The sensitivity labels are available for use in:
- emails (thick client and Outlook Web Access and mobile platforms)
- documents (all office documents, including the web versions of the applications).
Labelling for Microsoft Teams has recently been released for general availability and will be covered in upcoming revisions of this guide. This will ensure that labels can be applied to Microsoft Teams, Microsoft 365 groups and SharePoint sites.
Collaboration
The CAAS security model enables cross-agency collaboration between 2 consenting organizations using Teams, SharePoint Online and Planner.
The Teams application provides the following collaboration functionality using several Microsoft supporting products:
- individual and group chat/instant messaging
- individual and group voice call
- individual and group video call
- voicemail
- document collaboration
- screen and application sharing
- online meetings
- email-enabled channels
- organisation chart
- planning.
Collaboration between organizations assessed and operating at the same security level is straightforward. Collaboration between organizations operating on networks that have been assessed at different security levels presents extra considerations and risk.
The extra risks and considerations include:
- personnel clearances
- physical security requirements and the secure creation, storage and destruction of physical artefacts.
Considerations need to be assessed for security risk on a case-by-case basis.
Collaboration is initially controlled by lists of allowed domains. Individual users from those allowed external domains can then be invited individually to participate into Microsoft Teams as guests. D
Zero Trust security model
“Zero Trust” is an IT security concept where the organization does not automatically trust the user, the device they’re on, or the network location they’re connecting from.
Implementing Zero Trust lowers the agency’s risk profile and increases business agility as new devices and applications can be adopted faster.
The CAAS security model implements the Zero Trust concept through M365 features like requiring device enrolment with conditional access and enforcing Azure Active Directory Identity Protection.
For more information, review Microsoft’s Zero Trust Security Model and Framework.
Security
The compliance concepts covered by this guide will enable an organization to conduct a security assessment. Relevant documentation an agency can develop from this guide include:
- a system security plan
- a security risk management plan
- an incident response plan
- standard operating procedures.
Design decisions
The CAAS security model is designed to meet the requirements for CMMC 2.0 Level 2 once fully developed, NIST SP 800-171 R2 in the interim. The model secures Windows 10/11 desktops that have been onboarding into Microsoft Intune and has been developed with Microsoft and tested with independent security assessors.
The following tables describe the design decisions applicable to all organizations and implementation types.
Design Decisions for all agencies and implementation types.
| Decision point | Design decision | Justification |
|---|---|---|
| Azure AD Identity Protection | Configured | Azure AD Identity Protection is a tool that allows organizations to accomplish 3 key tasks: * automate the detection and remediation of identity-based risks. * investigate risks using data in the portal. * export risk detection data to a utility for further analysis. |
| Azure AD Multi-Factor Authentication (MFA) | Configured | Azure AD MFA will be enabled to meet CMMC compliance. |
| Enterprise collaboration | Teams and SharePoint Online | Teams and SharePoint Online will be used for enterprise collaboration. |
| Enterprise email | Exchange Online | Exchange Online and Microsoft Outlook will be deployed for the enterprise email solution. |
| Enterprise file storage | SharePoint Online / OneDrive | SharePoint Online and OneDrive will be deployed for enterprise file storage. |
| Conditional access policies | Configured | Conditional access allows control of the devices and apps that allow connection to email and company resources depending on location. |
| Remote access | Limited access depending on the device | Conditional access policies will limit what users can do while logging in remotely from an unmanaged device - such as view and edit in the browser without an ability to download or print |
| Identity | Azure Active Directory (Azure AD) | Azure AD will be the identity source. No on-premises active directory exists. |
| Device standard operating environment deployment | Configured | Device configuration will be deployed using Microsoft Autopilot and ongoing configuration will be controlled using Intune. (Not available in GCC High) |
| Workstation policy management | Configured | Workstation policy will be deployed and managed using Microsoft Intune. |
| Windows updates and patches | Configured | Configuration of Windows and third-party updates will be managed using Microsoft Intune. |
