Automated Alerts & Reporting
Overview
Your security baseline includes the configuration of a large number of automated alerts that will notify Compliance Managers of any detected threats in real-time. Alerts with a designation of High Severity are configured to automatically open a support ticket with Nimbus Logic Government support.
Custom reports are also compiled on a regularly scheduled basis and sent by email to Compliance Managers for review. These reports provide valuable insight into user and device compliance status
Scheduled Reports
Your Azure tenant has been configured with an Automation routine to automatically email Compliance Managers with important compliance reports and statistics on a weekly basis.
The following reports will be attached to the email only if data is present:
- Device listing for devices not identified as being compliant (Noncompliant, Not evaluated or In grace period)
- User listing identifying users with last sign-in activity over 30 days ago
- Malware report
- Defender agent status
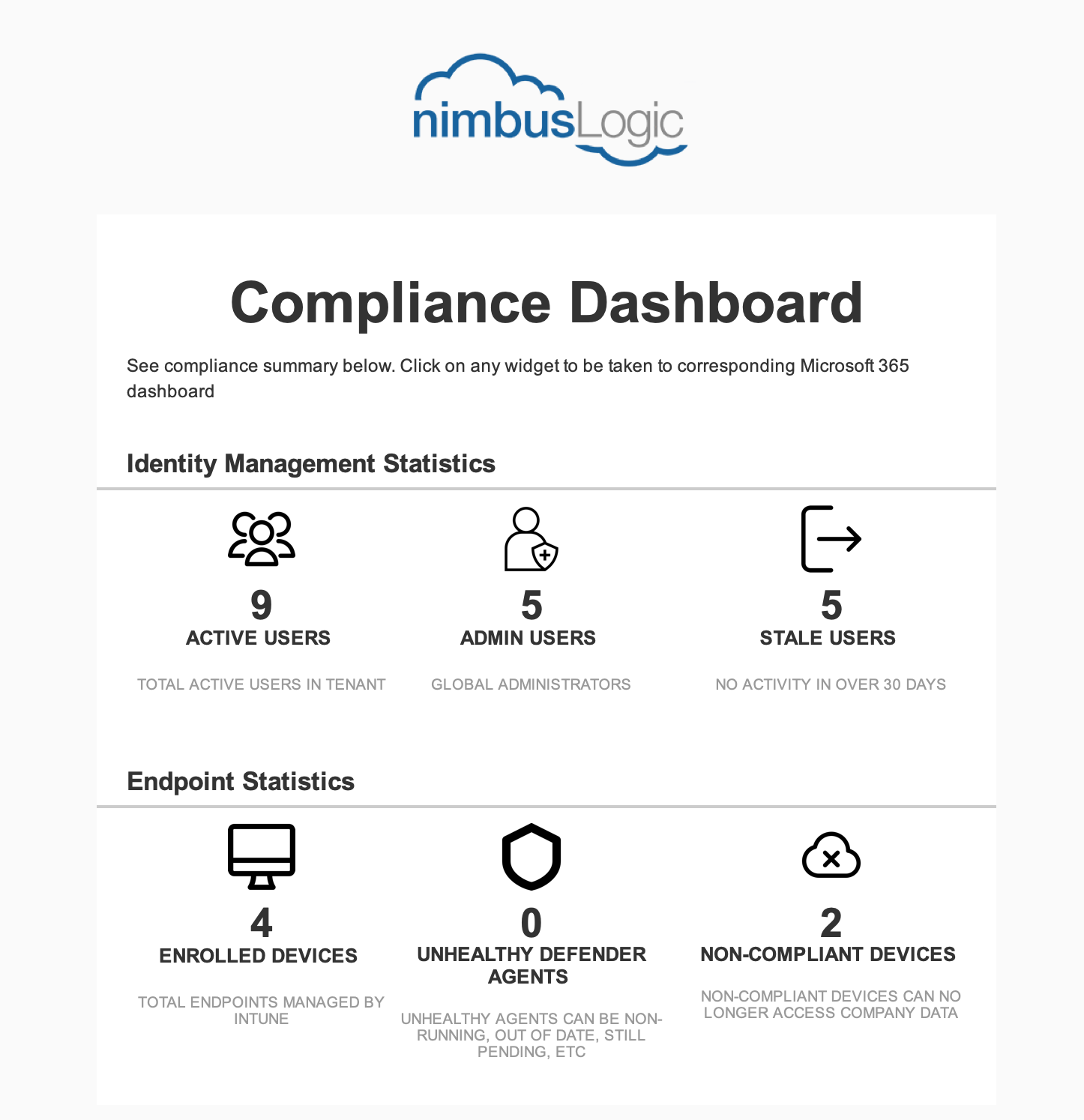
Statistics will be provided for
- Total active users in tenant
- Number of active Global Administrators
- Stale users with no activity in over 30 days
- Number of Enrolled Devices
- Non-Compliant device count
- Count of Unhealthy Defender Agents
Compliance Alerts
Enrolled devices are continually scanned to validate that they are meeting the security baselines defined within the CAAS documentation. If a device falls out of compliance, it has a 7 day grace period to come back into compliance or otherwise lose access to corporate data.
Below are the alerts defined once a device falls out of a compliant status. These alerts are designed to warn the end user that their device has been deemed as non compliant and they will lose access to corporate data unless action is taken.
| Alert Type | Recipient |
|---|---|
| Device is out of compliance - 7 day warning | Device Owner |
| Device is out of compliance - 3 day warning | Device Owner / Nimbus Logic Support |
| Device is out of compliance - 24 hour warning | Device Owner / Nimbus Logic Support |
Sample Alert Text
Subject: Your device is no longer compliant: X day warning
Message: Your device currently doesn’t meet security requirements and has been marked as out of compliance. Your device will lose access to company data in X days if security requirements are not met.
To view security requirements that must be met, please open the Company Portal app. For additional assist resolving compliance issues, please email support@nimbus-logic.us.
Thank You.
Security Alerts
Low Severity Alerts
Low severity alerts do not generate email alerts, but are visible any time via the corresponding dashboards.
- NIST - Malware in Email
Low severity alert that is triggered when incoming email surpasses 3 messages in 60 minutes, all containing malware. - MIP AutoLabel simulation completed
Low severity alert triggered when AutoLabel policy simulation(s) have been completed. - Successful exact data match upload
Low severity alert triggered to notify when new sensitive information was uploaded and is ready to be protected. - Elevation of Exchange admin privilege
Low severity alert that is triggered when someone in your organization becomes an Exchange admin or gets new Exchange admin permissions. - Malware campaign detected and blocked
Low severity alert triggered when an unusual amount of malware attacks were detected and blocked by Office 365. This alert will trigger in the event of one single event, and does not require accumulation. - Email reported by user as malware or phish
Low severity alert that is triggered when any email message is reported as malware or phish by users. This requires a manual submission by a user.
Medium Severity Alerts
- NIST - DLP Rules
Medium severity alert that is triggered 5 activities match a DLP incident condition within a period of 60 minutes. - Suspicious email sending patterns detected
Medium severity alert that is triggered when a user has been detected as sending suspicious messages (that match a DLP policy) outside of the organization and will be restricted if this activity continues. - Unusual volume of file deletion
This medium severity alert is triggered when the volume of files deleted in your organization becomes unusual. - Email sending limit exceeded
Medium severity alert that is triggered when a user has exceeded their email sending limit, which is set by default in Exchange’s Outboudn Spam policy as a maximum of 100 sent emails (internal or external) with a daily maximum of 1000. Once the condition is met, the user will be restricted from sending email until the following day. - Unusual increase in email reported as phish
This medium severity alert is triggered when there is a sharp increase in email messages reported as phish by users. - Unusual volume of external file sharing
This medium severity alert is triggered when the volume of external file sharing activities in your organization becomes unusual.
High Severity Alerts
- User restricted from sharing forms and collecting responses
This is a high severity alert, in which Microsoft Forms has identified repeated phishing attempts by a user in your tenant. This alert is to inform that this user is now blocked from sharing forms and collecting responses. - HVE A potentially malicious URL click was detected
High severity alert that is triggered when we have detected that one of your HVE users has recently clicked on a link that was found to be malicious. - Unusual external user file activity
High severity alert that is triggered when the volume of external user file activities in your organization becomes unusual. - Malware campaign detected in SharePoint and OneDrive
High severity alert that is triggered when the volume of malware/virus campaign detected in SharePoint and OneDrive in your organization becomes unusual. - Potential Nation-State Activity
High severity alert that is triggered when Microsoft Threat Intelligence Center detects an attempt to compromise accounts from your tenant. - User restricted from sending email
High severity alert - occurs when a user has been restricted from sending messages outside the organization due to potential compromised activity. - Form blocked due to potential phishing attempt
High severity alert that is triggered when Microsoft Forms detects a potential phishing attempt from a form and blocked it from distribution and response collection. - Suspicious Email Forwarding Activity
High severity. This alert is triggered once suspicious email forwarding is detected.
*Messages have been delayed
High severity. When Office 365 can’t deliver a message to your on-premises or partner servers via a connector, the message is queued in Office 365. This alert is triggered when the number of queued messages exceeds the policy threshold and have been queued for more than an hour. - Tenant restricted from sending unprovisioned email
This high severity alert will be triggered if/when the majority of traffic related to unprovisioned domains from this tenant has been detected as suspicious and the tenant has been restricted from sending email with unregistered domains. Investigate any potentially compromised user/admins, new connectors, or open relays and contact support to unblock your tenant. - Tenant restricted from sending email
High severity - The majority of traffic from this tenant has been detected as suspicious and has resulted in a ban on sending ability for the tenant. Ensure that any compromises or open relays have been resolved, and then contact support through your regular channel. - Failed exact data match upload
High severity alert that is triggered when new sensitive information fails to upload. - Malware campaign detected after delivery
High severity. Occurs when Office 365 detects malware in email messages delivered to users in your organization. You should investigate and remediate using an Incident in the Security and Compliance center. - Form flagged and confirmed as phishing
High severity. Alert triggered when a form created in Microsoft Forms from within your organization has been identified as phishing through Report Abuse and confirmed as phishing. - A potentially malicious URL click was detected
High severity alert triggered when we have detected that one of your users has recently clicked on a link that was found to be malicious.
Informational Alerts
- Email messages removed after delivery
Informational alert that is triggered because malicious emails were delivered and then later removed. - Email messages from a campaign removed after delivery
Informational alert triggered when email messages from a campaign were delivered and later removed. - Email messages containing phish URLs removed after delivery
Informational alert triggered when emails containing phishing URLs that were delivered and later removed. - Emails with malware that were delivered and later removed
Informational alert triggered when emails containing malware were delivered and later removed. - Email messages containing malicious URL removed after delivery
Informational alert triggered when emails containing malcious URLs were delivered and later removed. - Email messages containing malicious file removed after delivery
Informational alert triggered when emails containing a malicious file was delivered and then later removed. - eDiscovery search started or exported
This alert is triggered when users start content searches or eDiscovery searches or when search results are downloaded or exported. - Creation of forwarding / redirect rule
This alert is triggered when someone in your organization sets up auto-forwarding, email forwarding, redirect rule or a mail flow rule. - Admin triggered user compromise investigation
Medium severity alert that is triggered when an admin triggers an investigation of a user. - Admin triggered manual investigation of email
Informational alert that is triggered because an admin triggered manual investigation of an Email from explorer. - User requested to release a quarantined message
Informational alert notifying that a user has requested to release an email from quarantine. - Phish delivered because a user’s Junk Mail Folder is disabled
Informational alert triggered when a message containing phish was delivered because a user’s Junk Mail Folder is disabled. - Remediation action taken by admin on emails or URL or sender
This informational alert is triggered when an admin takes remediation action on the selected entity. - Creation of forwarding/redirect rule
This informational alert is triggered when someone in your organization sets up auto-forwarding, email forwarding, redirect rule or a mail flow rule. - Phish delivered due to an ETR override
This informational alert fires when message containing phish was delivered due to an ETR override. - Malware not zapped because ZAP is disabled
This informational alert fires when message containing malware was not zapped because ZAP is disabled. - Phish delivered due to an IP allow policy
This informational alert is triggered when a message containing a phish was delivered due to an IP allow policy. - Phish not zapped because ZAP is disabled
This informational alert fires when message containing phish was not zapped because ZAP is disabled. - Tenant Allow/Block List entry is about to expire
Informational alert notifying that a Tenant Allow/Block List entry will be removed due to expiration.
Microsoft Defender for Cloud Apps
Category: Threat Detection
Low Severity Alerts
- Leaked Credentials
When cybercriminals compromise valid passwords of legitimate users, they often share those credentials. This is usually done by posting them publicly on the dark web or paste sites or by trading or selling the credentials on the black market. - Misleading publisher name for an OAuth app
This policy scans the OAuth apps connected to your environment and triggers an alert when an app with a misleading publisher name is detected. Misleading publisher names, such as foreign letters that resemble Latin letters, could indicate an attempt to disguise a malicious app as an app coming from a known and trusted publisher.
Medium Severity Alerts
- Multiple delete VM activities
This policy profiles your environment and triggers alerts when users perform multiple delete VM activities in a single session with respect to the baseline learned, which could indicate an attempted breach. - Suspicious inbox manipulation rule
This policy profiles your environment and triggers alerts when suspicious inbox manipulation rules are set on a user’s inbox. This may indicate that the user account is compromised, and that the mailbox is being used to distribute spam and malware in your organization. - Ransomware activity
This policy profiles your environment and triggers alerts when an activity pattern is detected that is typical of a ransomware attack. - Unusual impersonated activity (by user)
This policy profiles your environment and triggers alerts when users perform multiple impersonated activities in a single session with respect to the baseline learned, which could indicate an attempted breach. - Unusual file download (by user)
This policy profiles your environment and triggers alerts when users perform multiple file download activities in a single session with respect to the baseline learned, which could indicate an attempted breach. - Unusual file deletion activity (by user)
This policy profiles your environment and triggers alerts when users perform multiple file deletion activities in a single session with respect to the baseline learned, which could indicate an attempted breach. - Activity performed by terminated user
This policy profiles your environment and alerts when a terminated user performs an activity in a sanctioned corporate application. This may indicate malicious activity by a terminated employee who still has access to corporate resources. - Impossible travel
This policy profiles your environment and triggers alerts when activities are detected from the same user in different locations within a time period that is shorter than the expected travel time between the two locations. This could indicate that a different user is using the same credentials. Detecting this anomalous behavior necessitates an initial learning period of 7 days during which it learns a new user’s activity pattern. - Activity from suspicious IP addresses
This policy profiles your environment and triggers alerts when activity is detected from an IP address that has been identified as risky by Microsoft Threat Intelligence. These IP are involved in malicious activities, such as botnets C&C, and may indicate a compromised account. - Suspicious inbox forwarding
This policy profiles your environment and triggers alerts when suspicious inbox forwarding rules are set on a user’s inbox. This may indicate that the user account is compromised, and that the mailbox is being used to exfiltrate information from your organization. - Activity from anonymous IP addresses
This policy profiles your environment and triggers alerts when it identifies activity from an IP address that has been identified as an anonymous proxy IP address. These proxies are used by people who want to hide their device’s IP address, and may be used for malicious intent. - Suspicious Power BI report sharing
This policy profiles your environment and triggers alerts when a user shared a Power BI report that may include sensitive information and may indicate a compromised account. The report was either shared with an external email address, published to the web, or a snapshot was delivered to an externally subscribed email address. - Unusual file share activity (by user)
This policy profiles your environment and triggers alerts when users perform multiple file sharing activities in a single session with respect to the baseline learned, which could indicate an attempted breach. - Multiple VM creation activities
This policy profiles your environment and triggers alerts when users perform multiple create VM activities in a single session with respect to the baseline learned, which could indicate an attempted breach. - Unusual administrative activity (by user)
This policy profiles your environment and triggers alerts when users perform multiple administrative activities in a single session with respect to the baseline learned, which could indicate an attempted breach. - Activity from infrequent country
This policy profiles your environment and triggers alerts when activity is detected from a location that was not recently or never visited by the user or by any user in the organization. Detecting anomalous locations necessitates an initial learning period of 7 days, during which it does not alert on any new locations. - Multiple failed login attempts
This policy profiles your environment and triggers alerts when users perform multiple failed login activities in a single session with respect to the baseline learned, which could indicate an attempted breach. - Multiple Power BI report sharing activities
This policy profiles your environment and triggers alerts when users perform multiple share report in PowerBI activities in a single session with respect to the baseline learned, which could indicate an attempted breach. - Multiple storage deletion activities
This policy profiles your environment and triggers alerts when users perform multiple storage deletion or DB deletion activities in a single session with respect to the baseline learned, which could indicate an attempted breach. - Preview: Suspicious file access activity (by user)
This detection policy profiles your environment and triggers alerts when users access multiple files from Microsoft SharePoint or Microsoft OneDrive. An alert is triggered only if the number of accessed files is uncommon for the user and the files might contain sensitive information. - Preview: Investigation Priority Score Increased
This policy profiles your current users investigation priority levels and triggers alerts on sudden relative increase of a user’s investigation priority. - Suspicious OAuth app file download activities
This policy scans the OAuth apps connected to your environment and triggers an alert when an app downloads multiple files from Microsoft SharePoint or Microsoft OneDrive in a manner that is uncommon for the user. - Suspicious email deletion activity (by user)
This policy profiles your environment and triggers alerts when a user performs suspicious email deletion activities in a single session, which could indicate an attempted breach. - Suspicious change of CloudTrail logging service
This policy profiles your environment and triggers alerts when users perform suspicious changes to the CloudTrail logging service, which could indicate an attempted breach. - Unusual addition of credentials to an OAuth app
This detection policy profiles your environment and triggers alerts when users perform unusual addition of credentials to an OAuth app activities, which could indicate an attempted breach. - Suspected over-pass-the-hash attack (encryption downgrade)
Encryption downgrade is a method of weakening Kerberos by downgrading the encryption level of different fields of the protocol that are usually encrypted using the highest level of encryption. A weakened encrypted field can be an easier target to offline brute force attempts. Various attack methods utilize weak Kerberos encryption cyphers. In this detection, Azure ATP learns the Kerberos encryption types used by computers and users, and alerts you when a weaker cypher is used that: (1) is unusual for the source computer and/or user; and (2) matches known attack techniques. In an Overpass-the-Hash attack an attacker can use a weak stolen hash in order to create a strong ticket, with a Kerberos AS request. In this detection, the AS_REQ message encryption type from the source computer was downgraded compared to the previously learned behavior (that is, the computer was using AES). - Honeytoken activity
Honeytoken accounts are decoy accounts set up to identify and track malicious activity that involves these accounts. Honeytoken accounts should be left unused, while having an attractive name to lure attackers (for example, SQL-Admin). Any activity from them might indicate malicious behavior. - Suspicious communication over DNS
Attacker on an effected computer may abuse the DNS protocol, which is often less monitored and is rarely blocked, for malicious activity. Malicious communication could be used for data exfiltration, command and control, or evading corporate network restrictions. - Suspicious service creation
A suspicious service has been created on a domain controller in your organization. This alert relies on event 7045 in order to identify this suspicious activity. - Suspicious additions to sensitive groups
Attackers add users to highly privileged groups. They do so to gain access to more resources and to gain persistency. The detection relies on profiling the group modification activities of users, and alerting when an abnormal addition to a sensitive group is seen. Profiling is continuously performed by ATP. - Remote code execution attempt
Attackers who compromise administrative credentials or use a zero-day exploit can execute remote commands on your domain controller. This can be used for gaining persistency, collecting information, denial of service (DOS) attacks or any other reason. Azure ATP detects PSexec and
Remote WMI connections. - Suspicious VPN connection
Azure ATP learns the entity behavior for users VPN connections over a sliding period of one month. The VPN-behavior model is based on the following activities: the computers the users logged in to and the locations the users connect from. An alert is opened when there is a deviation from the user’s behavior based on machine learning algorithm. - User and IP Address Reconnaissance (SMB)
Enumeration using Server Message Block (SMB) protocl, enables attackers to get information about where users recently logged on. Once attackers have this information, they can move laterally in the network to get to a specific sensitive - User and group membership reconnaissance (SAMR)
User and group membership reconnaissance is used by attackers to map the directory structure and target privileged accounts for later steps in an attack. The Security Account Manager Remote (SAM-R) protocol is one of the methods used to query the directory to perform such mapping. In this detection, no alerts would be triggered in the first month after Azure ATP is deployed. During the learning period, Azure ATP profiles which SAM-R queries are made from which computers, both enumeration and individual queries of sensitive accounts. - Suspected brute force attack (Kerberos, NTLM)
In a brute-force attack, an attacker attempts to authenticate with many different passwords for different accounts until a correct password is found for at least one account. Once found, an attacker can log in using that account. In this detection, an alert is triggered when many authentication failures using Kerberos or NTLM occurred, this can be either horizontally with a small set of passwords across many users; or vertically with a large set of passwords on just a few users; or any combination of these two options. The minimum period before an alert can be triggered is one week. - Suspected skeleton key attack (encryption downgrade)
Encryption downgrade is a method of weakening Kerberos by downgrading the encryption level of different fields of the protocol that are usually encrypted using the highest level of encryption. A weakened encrypted field can be an easier target to offline brute force attempts. Various attack methods utilize weak Kerberos encryption cyphers. In this detection, Azure ATP learns the Kerberos encryption types used by computers and users, and alerts you when a weaker cypher is used that: (1) is unusual for the source computer and/or user; and (2) matches known attack techniques. Skeleton Key is malware that runs on domain controllers and allows authentication to the domain with any account without knowing its password. This malware often uses weaker encryption algorithms to hash the user’s passwords on the domain controller. In this detection, the encryption method of the KRB_ERR message from the domain controller to the account asking for a ticket was downgraded compared to the previously learned behavior. - Suspected Golden Ticket usage (encryption downgrade)
Encryption downgrade is a method of weakening Kerberos by downgrading the encryption level of different fields of the protocol that are usually encrypted using the highest level of encryption. A weakened encrypted field can be an easier target to offline brute force attempts. Various attack methods utilize weak Kerberos encryption cyphers. In this detection, Azure ATP learns the Kerberos encryption types used by computers and users, and alerts you when a weaker cypher is used that: (1) is unusual for the source computer and/or user; and (2) matches known attack techniques. In a Golden Ticket alert, the encryption method of the TGT field of TGS_REQ (service request) message from the source computer was downgraded compared to the previously learned behavior. This is not based on a time anomaly (as in the other Golden Ticket detection). In addition, there was no Kerberos authentication request associated with the previous service request detected by ATP. - Account enumeration reconnaissance
In account enumeration reconnaissance, an attacker uses a dictionary with thousands of user names, or tools such as KrbGuess to attempt to guess user names in your domain. The attacker makes Kerberos requests using these names in order to try to find a valid username in your domain. If a guess successfully determines a username, the attacker gets the Kerberos error Preauthentication required instead of Security principal unknown. In this detection, Azure ATP can detect where the attack came from, the total number of guess attempts and how many were matched. If there are too many unknown users, Azure ATP detects it as a suspicious activity. - Suspected brute force attack (LDAP)
In a brute-force attack, an attacker attempts to authenticate with many different passwords for different accounts until a correct password is found for at least one account. Once found, an attacker can log in using that account. In this detection, an alert is triggered when Azure ATP detects a massive number of simple bind authentications. This can be either horizontally with a small set of passwords across many users; or vertically” with a large set of passwords on just a few users; or any combination of these two options. - Network mapping reconnaissance (DNS)
Your DNS server contains a map of all the computers, IP addresses, and services in your network. This information is used by attackers to map your network structure and target interesting computers for later steps in their attack. - Suspected overpass-the-hash attack (Kerberos)
Attackers use tools that implement various protocols (SMB, Kerberos, NTLM) in non-standard ways. While this type of network traffic is accepted by Windows without warnings, Azure ATP is able to recognize potential malicious intent. The behavior is indicative of techniques such as Over-Pass-the-Hash and brute force, as well as exploits used by advanced ransomware, for example, WannaCry. - Suspected WannaCry ransomware attack
Attackers use tools that implement various protocols (SMB, Kerberos, NTLM) in non-standard ways. While this type of network traffic is accepted by Windows without warnings, Azure ATP is able to recognize potential malicious intent. The behavior is indicative of techniques such as Over-Pass-the-Hash and brute force, as well as exploits used by advanced ransomware, for example, WannaCry. - Suspected NTLM authentication tampering
In June 2019, Microsoft published Security Vulnerability CVE-2019-1040, announcing discovery of a new tampering vulnerability in Microsoft Windows, when a “man-in-the-middle” attack is able to successfully bypass NTLM MIC (Message Integrity Check) protection. Malicious actors that successfully exploit this vulnerability have the ability to downgrade NTLM security features, and may successfully create authenticated sessions on behalf of other accounts. Unpatched Windows Servers are at risk from this vulnerability. In this detection, an Azure ATP security alert is triggered when NTLM authentication requests suspected of exploiting security vulnerability identified in CVE-2019-1040 are made against a domain controller in the network. - Suspected NTLM relay attack (Exchange account)
An Exchange Server can be configured to triggered NTLM authentication with the Exchange Server account to a remote http server run by an attacker. This server waits for the Exchange Server communication to relay its own sensitive authentication to any other server, or even more interestingly to the Active Directory over LDAP, and grabs the authentication information. Once the relay server receives the NTLM authentication, it provides a challenge that was originally created by the target server. The client responds to the challenge, preventing an attacker from taking the response, and using it to continue NTLM negotiation with the target domain controller. In this detection, an alert is triggered when Azure ATP identify use of Exchange account credentials from a suspicious source. - Suspected use of Metasploit hacking framework
Attackers use tools that implement various protocols (SMB, Kerberos, NTLM) in non-standard ways. While this type of network traffic is accepted by Windows without warnings, Azure ATP is able to recognize potential malicious intent. The behavior is indicative of techniques such as use of the Metasploit hacking framework. - Security principal reconnaissance (LDAP)
Security principal reconnaissance is used by attackers to gain critical information about the domain environment. Information that helps attackers map the domain structure, as well as identify privileged accounts for use in later steps in their attack kill chain. Lightweight Directory Access Protocol (LDAP) is one the most popular methods used for both legitimate and malicious purposes to query Active Directory. LDAP focused security principal reconnaissance is commonly used as the first phase of a Kerberoasting attack. Kerberoasting attacks are used to get a target list of Security Principal Names (SPNs), which attackers then attempt to get Ticket Granting Server (TGS) tickets for. - Suspected brute force attack (SMB)
Attackers use tools that implement various protocols such as SMB, Kerberos, and NTLM in non-standard ways. While this type of network traffic is accepted by Windows without warnings, Azure ATP is able to recognize potential malicious intent. The behavior is indicative of brute force techniques. - Remote code execution over DNS
12/11/2018 Microsoft published CVE-2018-8626, announcing that a newly discovered remote code execution vulnerability exists in Windows Domain Name System (DNS) servers, where servers fail to properly handle requests. An attacker who successfully exploits the vulnerability could run arbitrary code in the context of the Local System Account. Windows servers currently configured as DNS servers are at risk from this vulnerability. In this detection, an Azure ATP security alert is triggered when DNS queries suspected of exploiting the CVE-2018-8626 security vulnerability are made against a domain controller in the network. - Pass the certificate
Pass-the-Certificate is a lateral movement technique in which attackers steal a certificate from one computer and use it to gain access to another computer by requesting Kerberos tickets using the stolen certificate. In this detection, a certificate is seen used on two (or more) different computers. - Active Directory attributes Reconnaissance using LDAP
Pass-the-Certificate is a lateral movement technique in which attackers steal a certificate from one computer and use it to gain access to another computer by requesting Kerberos tickets using the stolen certificate. In this detection, a certificate is seen used on two (or more) different computers. - Suspected Golden Ticket usage (AES encryption)
Attackers with domain admin rights can compromise the KRBTGT account. Using the KRBTGT account, they can create a Kerberos ticket granting ticket (TGT) that provides authorization to any resource. This fake TGT is called a “Golden Ticket” and allows attackers to achieve network persistence. In this detection the attacker KRBTGT AES hash to generate the ticket. - Unusual ISP for an OAuth App
This detection policy profiles your environment and triggers alerts when OAuth apps preform activities from an unusual ISP, which could indicate an attempted breach using a non-genuine OAuth provider.
High Severity Alerts
- Risky sign-in
Azure Active Directory (Azure AD) detects suspicious actions that are related to your user accounts. For each detected action, a record called a risk event is created. For more details, see Azure AD risk events. - Malicious OAuth app consent
This policy uses Microsoft Threat Intelligence to scan OAuth apps connected to your environment and triggers an alert when it detects a potentially malicious app that has been authorized. Malicious OAuth apps may be used as part of a phishing campaign in an attempt to compromise users. - Suspected Golden Ticket usage (forged authorization data)
Known vulnerabilities in older versions of Windows Server allow attackers to manipulate the Privileged Attribute Certificate (PAC), a field in the Kerberos ticket that contains a user authorization data (in Active Directory this is group membership), granting attackers additional privileges. - Suspected Golden Ticket usage (time anomaly)
Attackers with domain admin rights can compromise the KRBTGT account. Using the KRBTGT account, they can create a Kerberos ticket granting ticket (TGT) that provides authorization to any resource. This fake TGT is called a “Golden Ticket” and allows attackers to achieve network persistence. In this detection, an alert is triggered by a nonexistent account. - Suspected DCShadow attack(domain controller promotion)
A domain controller shadow (DCShadow) attack is an attack designed to change directory objects using malicious replication. This attack can be performed from any machine by creating a rogue domain controller using a replication process. DCShadow uses RPC and LDAP to: Register the machine account as a domain controller (using domain admin rights), and Perform replication (using the granted replication rights) over DRSUAPI and send changes to directory objects. In this detection, an alert is triggered when a machine in the network is trying to register as a rogue domain controller. - Suspected identity theft (pass-the-ticket)
Pass-the-Ticket is a lateral movement technique in which attackers steal a Kerberos ticket from one computer and use it to gain access to another computer by reusing the stolen ticket. In this detection, a Kerberos ticket is seen used on two (or more) different computers. - Suspected Golden Ticket usage (nonexistent account)
Attackers with domain admin rights can compromise the KRBTGT account. Using the KRBTGT account, they can create a Kerberos ticket granting ticket (TGT) that provides authorization to any resource. This fake TGT is called a “Golden Ticket” and allows attackers to achieve network persistence. Forged Golden Tickets of this type have unique characteristics this detection is specifically designed to identify. - Malicious request of Data Protection API master key
The Data Protection API (DPAPI) is used by Windows to securely protect passwords saved by browsers, encrypted files, and other sensitive data. Domain controllers hold a backup master key that can be used to decrypt all secrets encrypted with DPAPI on domain-joined Windows machines. Attackers can use that master key to decrypt any secrets protected by DPAPI on all domain-joined machines. In this detection, an alert is triggered when the DPAPI is used to retrieve the backup master key. - Suspected DCShadow attack(DC replication request)
Active Directory replication is the process by which changes that are made on one domain controller are synchronized with other domain controllers. Given necessary permissions, attackers can grant rights for their machine account, allowing them to impersonate a domain controller. The attackers will strive to initiate a malicious replication request, allowing them to change Active Directory objects on a genuine domain controller, which might give the attackers persistence in the domain. In this detection, an alert is triggered when a suspicious replication request is generated against a genuine domain controller protected by Azure ATP. The behavior is indicative of techniques used in domain controller shadow attacks. - Suspected Golden Ticket usage (ticket anomaly)
Attackers with domain admin rights can compromise the KRBTGT account. Using the KRBTGT account, they can create a Kerberos ticket granting ticket (TGT) that provides authorization to any resource. This fake TGT is called a “Golden Ticket” and allows attackers to achieve network persistence. Forged Golden Tickets of this type have unique characteristics this detection is specifically designed to identify. - Suspected DCSync attack (replication of directory services)
Active Directory replication is the process by which changes that are made on one domain controller are synchronized with all other domain controllers. Given necessary permissions, attackers can initiate a replication request, allowing them to retrieve the data stored in Active Directory, including password hashes. In this detection, an alert is triggered when a replication request is initiated from a computer that is not a domain controller. - Suspected identity theft (pass-the-hash)
Pass-the-Hash is a lateral movement technique in which attackers steal a user’s NTLM hash from one computer and use it to gain access to another computer. - _Suspected Golden Ticket usage (ticket anomaly using resource based constrained delegation)
Attackers with domain admin rights can compromise the KRBTGT account by setting resource bases constrained delegation for an account with SPN. Using the KRBTGT account, they can create a Kerberos ticket granting ticket (TGT) that provides authorization to any resource. This fake TGT is called a ‘Golden Ticket’ and allows attackers to achieve network persistence. Forged Golden Tickets of this type have unique characteristics this detection is specifically designed to identify. - Data exfiltration over SMB
Domain controllers hold the most sensitive organizational data. For most attackers one of their top priorities is to gain access to the domain controllers and steal your most sensitive data. For example exfiltration of the Ntds.dit file, stored on the DC, allows an attacker to forge Kerberos ticket granting tickets(TGT) that provide authorization to any resource, and set the ticket expiration to any arbitrary time. An Azure ATP alert is triggered when suspicious transfers of data are observed from domain controllers. - Suspected rogue Kerberos certificate usage
Rogue certificate is a persistence technique used by attackers after getting control over the organization. Attackers compromise the Certificate Authority server and generate certificates that might be used in the future as backdoor accounts. - Suspected SID-History injection
Adversaries may use this mechanism for privilege escalation. With Domain Administrator (or equivalent) rights, harvested or well-known SID values [3] may be inserted into SID-History to enable impersonation of arbitrary users/groups such as Enterprise Administrators. - Suspected Kerberos SPN exposure
Adversaries possessing a valid Kerberos ticket-granting ticket (TGT) may request one or more Kerberos ticket-granting service (TGS) service tickets for any SPN from a domain controller (DC). - Suspected AS-REP Roasting attack
AS-REP Roasting is an attack against Kerberos for user accounts that do not require preauthentication, allowing the attacker to perform brute force attacks against the users. - Suspected Netlogon privilege elevation attempt (CVE-2020-1472 exploitation)
An elevation of privilege vulnerability exists when an attacker establishes a vulnerable Netlogon secure channel connection to a domain controller, using the Netlogon Remote Protocol (MS-NRPC), aka ‘Netlogon Elevation of Privilege Vulnerability’. (CVE-2020-1472) - _Suspected AD FS DKM key read
This alert tries to find actors that try to read the DKM key of the AD FS object. - Suspected abnormal Exchange attribute change (CVE-2021-26855 exploitation)
This alert triggers when an attacker exploits the Exchange server in the domain and sets a backdoor for remote code execution (CVE-2021-26855 exploitation). - Suspected Windows Print Spooler service exploitation attempt (CVE-2021-34527)
This alert triggers when an attacker exploits the Windows Print Spooler service to improperly perform privileged file operations. - Suspicious network connection over Encrypting File System Remote Protocol
This attack allows an attacker to take over an Active Directory (AD) Domain by exploiting a flaw in the Encrypting File System Remote (EFSRPC) Protocol and chaining it with a flaw in Active Directory Certificate Services.
