Incident Response Plan
Purpose
The purpose of this Incident Response Plan (IRP) is to provide full transparency into Nimbus Logic’s role in detecting cybersecurity incidents, responding to and remediating them, and reducing the risk of recurrence. This IRP also outlines incident response tasks that the Organization seeking certification (OSC) is responsible for.
Scope
The scope of this IRP is specific to the use of Microsoft 365 services as part of the Compliance-as-a-Service (CAAS) product. It is a system-specific IRP and is designed to complement an OSC’s overarching IRP. This document will be updated over time based on evolving agency needs and lessons learned from cyber incidents.
Important Contact Information
Incident Response Team Contacts
| Role | Name | Cell Phone | |
|---|---|---|---|
| Incident Response Team Lead | Jason Smith | jsmith@nimbus-logic.com | 518-293-0550 |
| Incident Response Team Lead Backup | Gregory Rowe | greg@nimbus-logic.com | 518-331-3572 |
| Incident Responder | David Wilming | david@nimbus-logic.com | |
| Incident Responder & Forensic Analyst | Chris Denno | cdenno@nimbus-logic.com | |
| Incident Responder | Daniel Hurd | dhurd@nimbus-logic.com |
Incident Response Team Members & Roles
| Role | Name | Responsibilities |
|---|---|---|
| Incident Response Team Lead | Jason Smith | Coordinates response efforts, maintains response capability |
| Incident Responder(s) | Jason Smith, Gregory Rowe, David Wilming, Daniel Hurd, Chris Denno | Detects and contains incidents |
| Forensic Analyst | Jason Smith, Gregory Rowe, Chris Denno | Captures and analyzes system images and logs |
| Recovery Specialist | Jason Smith, Gregory Rowe | Recovers systems back to pre-incident condition |
Nimbus Logic (ESP) Tenant Roles
Role Assignments
This table outlines the assigned Azure roles and their status assigned to the ESP Incident Response Team (Nimbus Logic) leveraging Azure Privileged Identity Management (PIM).
- Active roles are permanently assigned and always available to the user.
- Eligible roles require just-in-time (JIT) activation when needed, enhancing security by reducing standing privileges.
| Role Category | Azure Role | Assignment Status |
|---|---|---|
| Entra ID Roles | Global Reader | Active |
| Global Admin | Eligible | |
| Azure Subscription Roles | Owner | Eligible |
| Sentinel Roles | Sentinel Reader | Active |
| Sentinel Contributor | Eligible |
Responsibilities
Nimbus Logic (ESP) Responsibilities
- Design, implement, and assess the security of the CAAS solution.
- Maintain security monitoring and logging capabilities.
- Provide Sentinel Reader permissions permanently for incident diagnosis.
- Maintain Global Admin as an eligible role, activated only through Privileged Identity Management (PIM) when necessary.
- Perform initial triage and analysis on security incidents.
- Coordinate remediation efforts with OSC Compliance Managers.
- Confirm Compliance Managers as defined in the by the OSC (User Role Assignments)
- Maintain an Incident Response Team (IRT) responsible for analyzing and addressing cybersecurity threats.
- Be sure to work with only Compliance Managers from the OSC in any kind of incident handling.
Organization seeking certification (OSC) Responsibilities
- Respond to incident alerts and work with Nimbus Logic to confirm false positives.
- Provide additional context when needed (e.g., user activity validation).
- Authorize and assist with user or device isolation when required.
- Maintain access to required Microsoft security and compliance portals.
- Participate in post-incident analysis and continuous improvement activities.
- Follow designated escalation procedures and communication protocols, and confirm availability of Compliance Managers during the time of Incident Response.
Incident Response Team (IRT) Responsibilities
- Execute the four-step NIST incident response life cycle.
- Maintain communication channels and escalation procedures.
- Document and review incidents for compliance adherence.
- Conduct forensic analysis and recommend corrective actions.
Definitions
- Event: Any observable occurrence in a network or system.
- Incident: A violation or imminent threat of violation of computer security policies, acceptable use policies, or standard security practices.
- Threat: The potential source of an adverse event.
- Vulnerability: A weakness in a system, application, or network that is subject to exploitation or misuse.
- Incident Handling: The mitigation of violations of security policies and recommended practices.
- Incident Response Team (IRT): The collaborative teams from the ESP (ESP Incident Response Team) and OSC (Compliance Managers).
Incident Response Plan
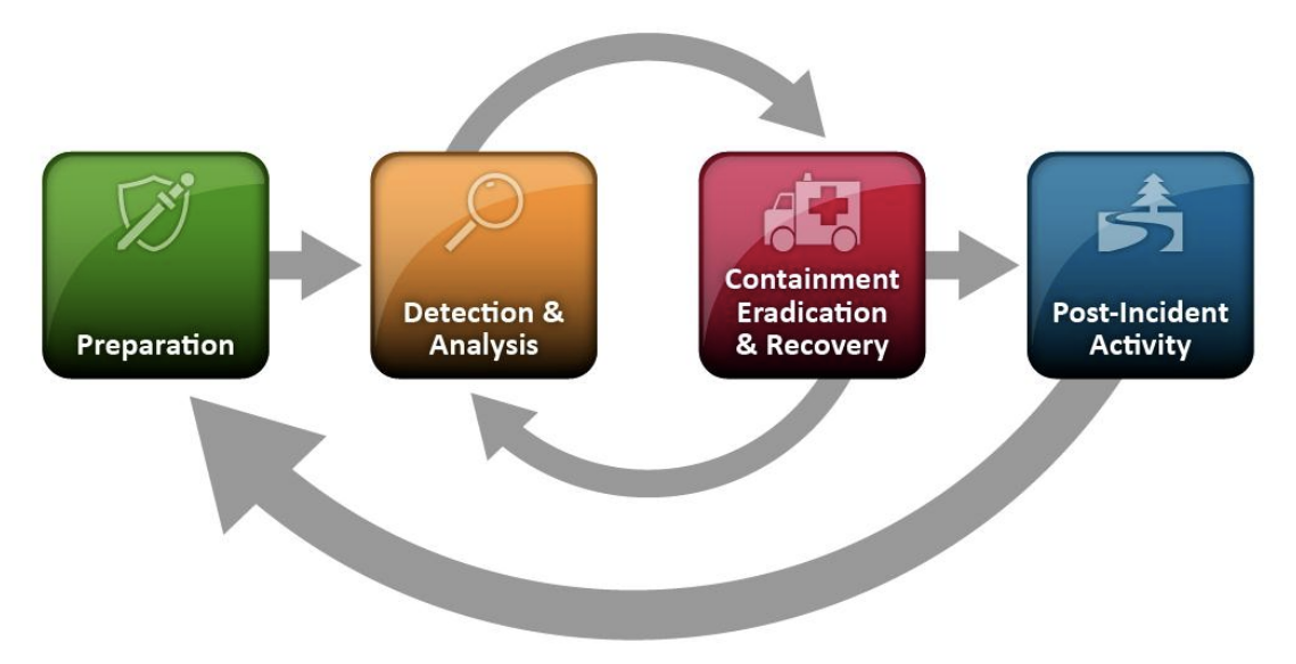
This IRP follows the four-step National Institute of Standards and Technology (NIST) incident response life cycle as documented in Special Publication 800-61 Revision 2:
Preparation
Detection & Analysis
Containment, Eradication, and Recovery
Post-Incident Activity
Microsoft Management Portals
Table 1a: Microsoft Management Portals (GCC)
| Portal | URL |
|---|---|
| Microsoft 365 Defender Portal | https://security.microsoft.com |
| Defender for Cloud Apps Portal | https://portal.cloudappsecurity.com |
| Azure portal (including Entra ID) | https://portal.azure.com |
| Microsoft 365 Purview Portal | https://purview.microsoft.com |
| Microsoft 365 Admin Center | https://admin.microsoft.com |
Table 1b: Microsoft Management Portals (GCC High)
| Portal | URL |
|---|---|
| Microsoft 365 Defender Portal | https://security.microsoft.us |
| Defender for Cloud Apps Portal | https://portal.cloudappsecurity.us |
| Azure portal (including Entra ID) | https://portal.azure.us |
| Microsoft 365 Purview portal | https://purview.microsoft.us/ |
| Microsoft 365 Admin Center | https://portal.office365.us/adminportal/ |
Incident Criticality Assessment
Table 2: Incident Criticality Definitions
| Incident Criticality | Performance Metrics |
|---|---|
| Extreme | Major impact on departmental outcomes and performance. Requires major additional management effort by Senior Executive to control the impact. Unavailability of agency mission-critical systems including the delivery of Government outcomes. Catastrophic breach and/or loss and/or destruction of agency information containing sensitive and personal information and/or controlled unclassified information. |
| High | Moderate impact on achievement of outcomes and performance. Requires additional management effort by business area, Senior Executive to control the impact. |
| Medium | Minor impact on achievement of outcomes and performance. Requires additional management effort within the business area to control the impact. Some adverse publicity. |
| Low | Insignificant impact on achievement of outcomes and performance. |
| None | No effect to the organization’s ability to provide all services to all users. |
Information Impact Categories
Table 3: Information Impact Categories
| Impact Category | Definition |
|---|---|
| None | No information was exfiltrated, changed, deleted, or otherwise compromised. |
| Privacy Breach | Sensitive personally identifiable information (PII) was accessed or exfiltrated. |
| Proprietary Breach | Unclassified proprietary information, such as protected critical infrastructure information (PCII), was accessed or exfiltrated. |
| CUI Breach | Controlled Unclassified Information (CUI) was changed or deleted. |
Incident Containment, Eradication, and Recovery
Table 4: Recoverability Effort Category
| Category | Definition |
|---|---|
| Regular | Time to recovery is predictable with existing resources. |
| Supplemented | Time to recovery is predictable with additional resources. |
| Extended | Time to recovery is unpredictable; additional resources and outside help are needed. |
| Not Recoverable | Recovery from the incident is not possible (e.g., sensitive data exfiltrated and posted publicly); launch investigation. |
Testing
This IRP aligns with NIST 800-171r2 and CMMC 2.0 standards and will be reviewed periodically for compliance updates and process enhancements.
